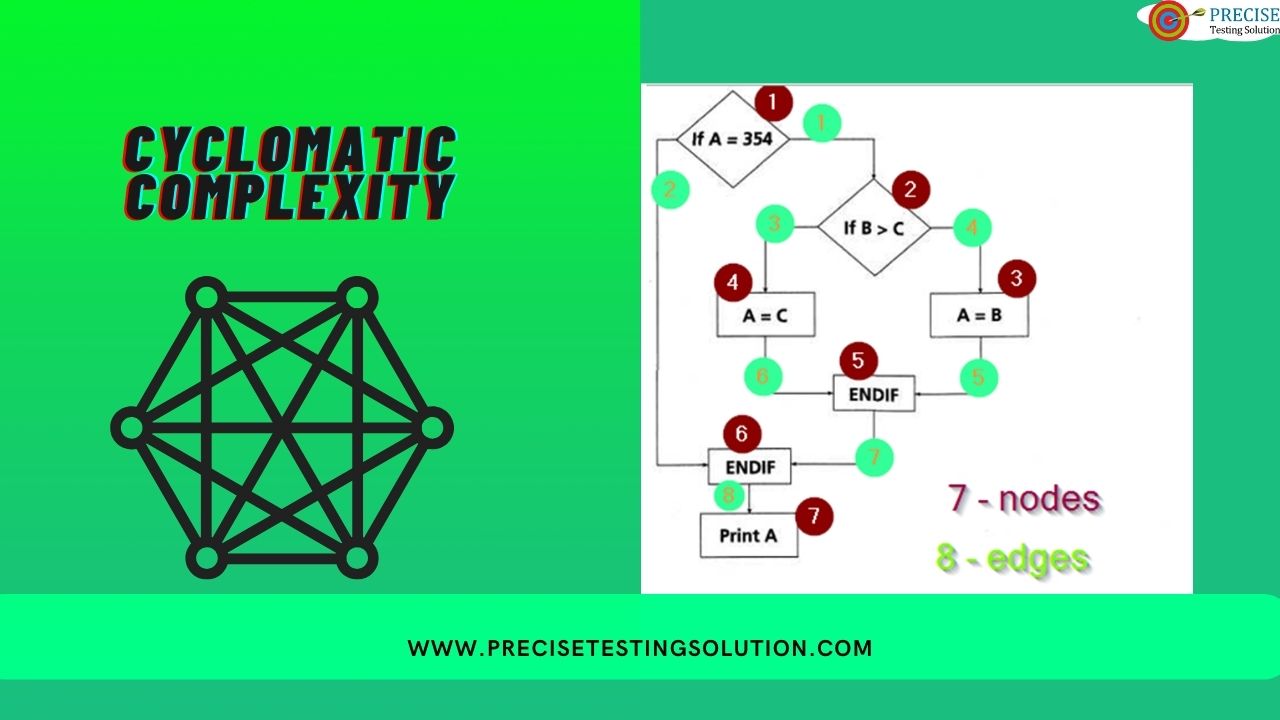
How to Identify Email Spoofing Attempts
What Is The History Of Spoofing Spoofing, in the context of cybersecurity, refers to the act of disguising the origin of a communication to deceive the recipient. This technique has a long history, predating the digital age. Early Forms:Voice Impersonation: Historical figures like Julius Caesar were known to have